Deep Assessment
RiskRecon asset discovery is engineered to be extraordinarily thorough while having an extremely low false-positive rate of less than 1%.
Asset Discovery
Our asset profiles are completely refreshed every two weeks, because even if a company owned an asset a month ago, it doesn't mean that they still do. At the heart of our asset discovery are analysts who train supervised machine learning models for each company monitored. These models enable RiskRecon to efficiently mine the internet for company systems and to ensure accurate company asset attribution as companies shift over time.
IT Profiling
RiskRecon builds a detailed profile of every asset discovered. This asset profile provides you with an intimate understanding of how the organization has constructed their business-computing architecture. This profile includes:
- Software
- IT Infrastructure
- Geolocation
- Hosting Providers
- Fourth Parties
- Domains
- Systems
- Configurations
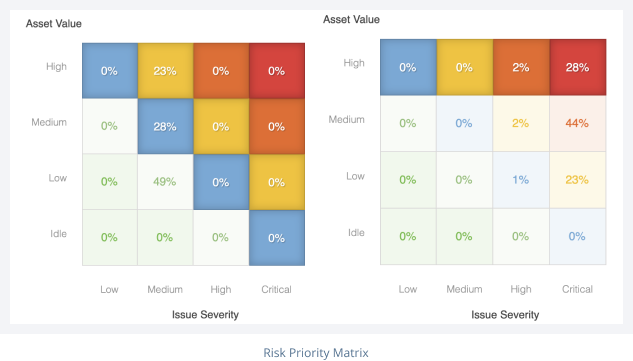
For each security domain, RiskRecon reports overall current performance, trends, and industry benchmarks. Each issue is backed with detailed information issue summary and detailed descriptions, related CVEs, hostname, IP address, asset value, issue severity, and risk priority.
Custom Risk Prioritization
We wanted a cyber risk assessment system that produced custom-tuned assessments to match risk appetite. So we built it.
Automatic data filtering
Just configure our policy and the alerting and action plans to send you the issues that matter most to you.
Risk prioritization
Stop digging through mountains of issues to get to the most important ones. With risk prioritization, you know exactly where to start.
My Risk Policy
Configuring RiskRecon to match your risk appetite is simple: For each inherent risk category, simply tune a risk policy for each security criterion.
Building on RiskRecon's unique capability to automatically risk prioritize issues, RiskRecon announced a cutting-edge capability that lets organizations automatically produce third-party cyber risk assessments and action plans that are custom-fitted to match their unique risk appetite.
In addition to automatically creating custom-fitted risk assessments and action plans, organizations can tune RiskRecon's continuous monitoring to show only the material risk issues that violate their risk policy.
Efficient
RiskRecon streamlines your vendor security risk management program, saving your third-party risk team time and money.
Maximize Efficiency
Get instant visibility of each vendor's compliance to your custom risk policy requirements. Engaging non-performing vendors is super easy just send them the action plan that details only the issues violating your risk policy. RiskRecon automatically and continuously assesses your vendors for compliance to your risk policy, making it easy for you to understand and act on your third-party risk.
Focus on the lowest-performing vendors
RiskRecon arms your management team with the information needed to allocate assessment resources based on risk. Instead of assessing vendors at a fixed frequency, you can adjust the assessment frequency based on vendor performance, assessing well-performing vendors less frequently than poor-performing ones.
RiskRecon's objective assessments give you insight into which vendors are performing well and which ones are problematic. Now you can allocate more resources to those performing poorly and fewer to those that are not.
Onboard new vendors faster
Evaluating vendors can take weeks, resulting in frustrating project delays. RiskRecon dramatically speeds up the process of initial vendor evaluation, providing you with a simple method to screen vendors. Compare the risk performance ratings of multiple vendors side by side and dive into the details to which ones best meet your risk performance requirements.
Assess existing vendors more efficiently
The goal of a third-party risk assessment is to determine if the vendor performs to your requirements. Unfortunately, analysts go into assessments blind, with minimal to no knowledge of the vendors' systems or security risk posture. This makes it difficult to conduct an efficient and informed assessment.
Manually assess only when necessary
RiskRecon arms your analysts with deep knowledge of your vendors IT environment security risk performance before ever engaging the vendor. This lets your vendors skip areas of strength and go deep into areas of weakness.
Automatically create action plans tuned to your risk priorities
It's easy to have your vendors address their problematic areas of risk: every RiskRecon vendor assessment has a share-ready action plan that contains only the issues that violate your risk policy. Email it or invite them to collaborate with you online.
Automatically verify vendor issue remediation
RiskRecon continuously monitors your vendors, frequently checking to see if they have addressed the issues you asked them to fix. As they fix the issues, their RiskRecon rating improves, and the issues are removed from the vendor action plan. Super simple.
Critical Vulnerability Management
When critical vulnerabilities hit, every resource is quickly employed to ensure the protection of your enterprise. With RiskRecon, remediation maximizes your resources so your enterprise stays secure.
|
|
Accurate
RiskRecon’s asset attribution is independently certified to 99.1% accuracy with a false positive rate below 1%.
Data Accuracy
Accuracy counts when assessing the risk third and fourth parties introduce into every enterprise organization. Without it, organizations are blind to where they are vulnerable.
Reducing that risk across the ecosystem of vendors you do business with is challenging when False Positives are present - and RiskRecon proves that it is providing the highest level of accuracy possible for customers.
RiskRecon’s asset attribution is independently certified to 99.1% accuracy. And we don’t hide any of the assessment details. It’s all visible to you and your vendors at no additional fee. Action requires accuracy and transparency. RiskRecon provides you both.




