Amazon Web Services Core Assessment Playbook & Questionnaire
A toolkit for assessing third-party cyber risks with AWS configurations

RiskRecon believes that third-party cybersecurity assessments founded on objective evidence are the most effective way to achieve good risk outcomes. This AWS Assessment Playbook and the accompanying Questionnaire do just that - they help you achieve better risk outcomes by providing you the knowledge and tools for objectively assessing the security quality of any Amazon Web Services deployment.
Benefits of the AWS Toolkit:
- Get a step-by-step methodology for assessing the security configurations of any AWS deployment
- Understand 33 essential AWS security assessment criteria
- Assessment-ready questionnaire

The Core Assessment Playbook provides a step-by-step methodology for assessing the quality of third-party security configurations of any Amazon Web Services deployment. In the asset, you will find essential AWS environment assessment security criteria, explanations of the importance of each criterion, how to gather related evidence, and what a proper configuration looks like.
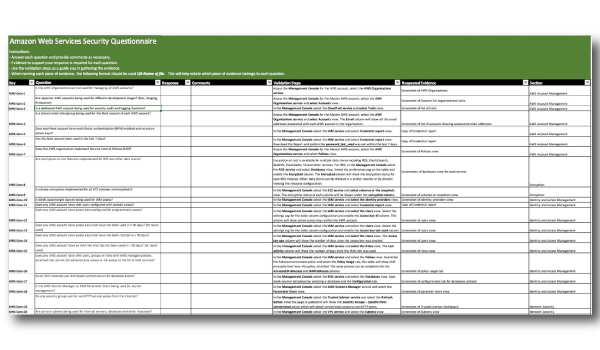
The Amazon Web Services Core Assessment Questionnaire can be used for third-party security risk assessments of AWS environments. Send it over to a vendor to fill out, or ask the questions over the phone. The depth of this sheet will allow you to gain a full understanding of any AWS configuration. You are likely going to learn that many of your vendors have significant gaps in their environments that previously were not discovered.

The AWS Core Security Criteria covers six security domains:
- AWS Account Management
- Encryption
- Identity and Access Management
- Network Security
- Detection and Monitoring
- Processes
Each domain contains one or more security criteria. Each criterion is presented in the Playbook as follows:
- ID - The unique criterion identifier. This maps to the associated questionnaire.
- Criterion - The assessment criterion, phrased as a question.
- Why this is important - An explanation of why the criterion is important for securing the AWS environment.
- Validation steps - A description of how to collect the evidence necessary to assess compliance with the criterion.
- Acceptable responses - A listing of the configuration states that meet the criterion requirements.
- Failure responses - A listing of the configuration states that do not meet the criterion requirements.
- More info - A hyperlink to additional information related to the criterion.
Follow us for the latest insights




